Okta-Unable to sign in
Might need more inforamtion on what you are trying to achieve here
So you have Okta as SSO or Identitiy Provider ? The same users are also in Active Directory where the roles are managed ?
You then want to Map the roles via your Optimizely Solution ?
Are you able to provide some code examples ?
I don't want to map the role from optimizely solution. I just want to validate the ad account through okta and get response success or fail response .
Here is my code:-
private void ConfigureOktaAuthentication(IServiceCollection services, IConfiguration configuration)
{
string OktaDomain = configuration.GetValue<string>("Okta:OktaDomain");
string OktaClientId = configuration.GetValue<string>("Okta:OktaClientId");
string OktaClientSecretKey = configuration.GetValue<string>("Okta:OktaClientSecretKey");
string BaseUrl = configuration.GetValue<string>("DreesSettings:BaseUrl");
if (BaseUrl.EndsWith("/"))
{
BaseUrl = BaseUrl.TrimEnd('/');
}
services.AddAuthentication(options =>
{
options.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
options.DefaultSignInScheme = CookieAuthenticationDefaults.AuthenticationScheme;
})
.AddCookie("okta")
.AddCookie(options =>
{
options.CookieManager = new SystemWebChunkingCookieManager() as ICookieManager;
})
.AddOktaMvc(new OktaMvcOptions
{
OktaDomain = OktaDomain,
AuthorizationServerId = "",
ClientId = OktaClientId,
ClientSecret = OktaClientSecretKey,
Scope = new List<string> { "openid", "profile", "email" },
CallbackPath = "/authorization-code/callback",
GetClaimsFromUserInfoEndpoint = true,
PostLogoutRedirectUri = $"{BaseUrl}/episerver/cms",
OpenIdConnectEvents = new OpenIdConnectEvents
{
OnAuthenticationFailed = context =>
{
context.HandleResponse();
context.Response.BodyWriter.WriteAsync(Encoding.ASCII.GetBytes(context.Exception.Message));
return Task.FromResult(0);
},
OnTokenValidated = (ctx) =>
{
var redirectUri = new Uri(ctx.Properties.RedirectUri, UriKind.RelativeOrAbsolute);
if (redirectUri.IsAbsoluteUri)
{
ctx.Properties.RedirectUri = redirectUri.PathAndQuery;
}
var claims = new List<Claim> { new Claim(ClaimTypes.Role, "WebAdmins"), new Claim(ClaimTypes.Role, "WebEditors") };
ctx.Principal.AddIdentity(new ClaimsIdentity(claims));
ServiceLocator.Current.GetInstance<ISynchronizingUserService>().SynchronizeAsync(ctx.Principal.Identity as ClaimsIdentity);
return Task.FromResult(0);
},
OnRedirectToIdentityProvider = context =>
{
if (context.Response.StatusCode == 401 &&
context.HttpContext.User.Identity.IsAuthenticated)
{
context.Response.StatusCode = 403;
context.HandleResponse();
}
if (context.Response.StatusCode == 401 && IsXhrRequest(context.Request))
context.HandleResponse();
return Task.CompletedTask;
}
}
});
}
private static bool IsXhrRequest(HttpRequest request)
{
const string xRequestedWith = "X-Requested-With";
var query = request.Query;
if ((query != null) && (query[xRequestedWith] == "XMLHttpRequest"))
return true;
var headers = request.Headers;
return (headers != null) && (headers[xRequestedWith] == "XMLHttpRequest");
}
Ive taken your code made some ammends and am able to login to Optimizely just fine please see here
Optimizely-Okta/OktaExtensions.cs at main · Netcel-Optimizely/Optimizely-Okta (github.com)
Im struggling to see any additional code which checks against AD (Active Directory)
If you are managing this all via Okta it might be worth returning the claim back and than assigning that user to WebEditors or WebAdmins group based on this
line 73
I apperciate your response, thank you so much.
I was also able to login fine with normal users . Normal user means I have added some user in okta site (Directory>People>Added some person) . But My aim is to login with AD users for that I have also configured some AD users into the okta site.
You are right , I have not added any addional code against AD (Active Directory) users. Do you have any Idea what code needs to be add ?
Please help..!
Thank You
Binay Thakur
I think the rest of your configuration now is at the Okta layer, have you looked at the AD Connector
https://www.okta.com/integrations/active-directory/
''When Okta is configured for delegated authentication to Active Directory, no AD credentials are stored in the cloud, and passwords never get out of sync. Unlike Windows Azure Active Directory and on-premises Azure AD Connect (DirSync), Okta maintains continuous connectivity with AD with its on-premises agents. When an AD user logs in, Okta agents check the password stored in AD in real-time.''
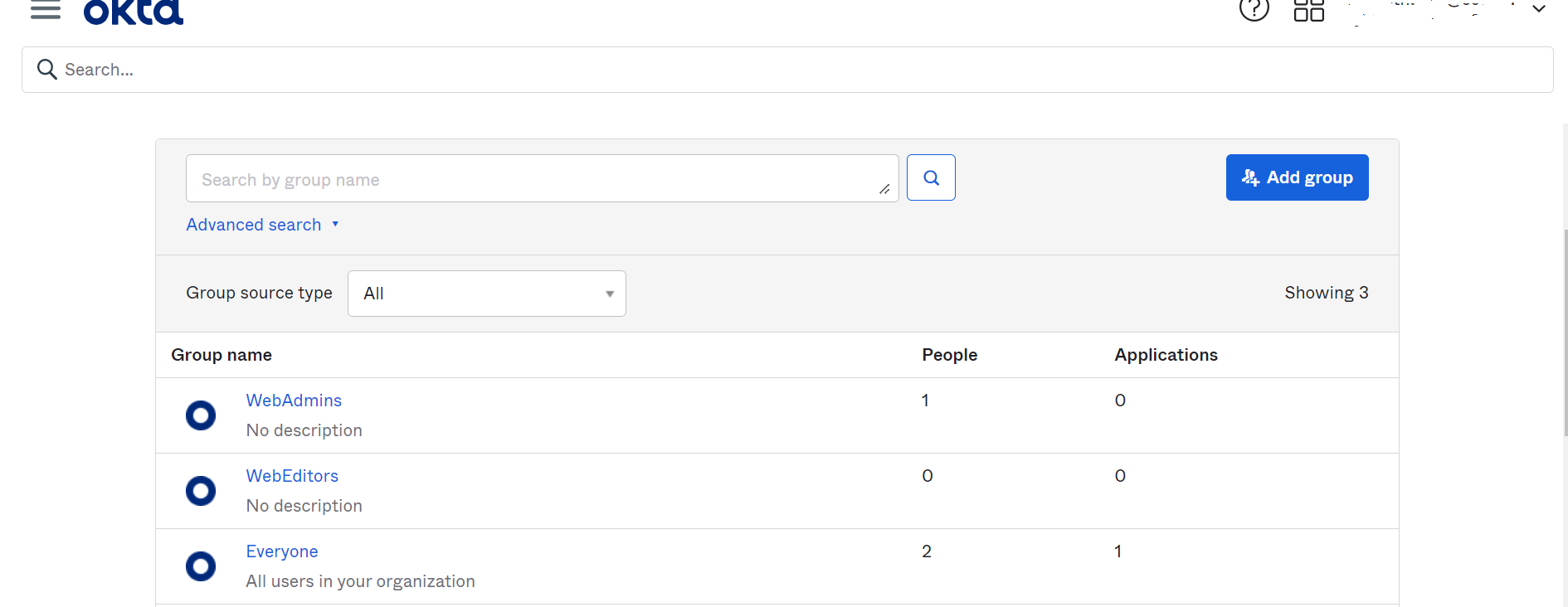
I have added few roles into the okta site and also mapped the role with users. Can you please help me to mapped the okta role and user permission into my applicatioin ?
I am not seeing the group into my application when I am logged in through the okta account.

Hi Team,
I have integrated okta login interface in my application and i am validating AD account with okta through my application but I am getting "Unable to sign in" error message . Below is error response from console.
{"errorCode":"E0000022","errorSummary":"The endpoint does not support the provided HTTP method","errorLink":"E0000022","errorId":"oaeIr0jTClfT0SUTTLyF8kEHQ","errorCauses":[]}
But I am able to login directly in okta website with the same AD account.
I am not sure whether it is configuration issue or coding issue. Anyone have any idea ?
Please help...!