This topic describes some typical actions such as mapping host names in the DNS and restricting edit access, when going live with sites in Optimizely Digital Experience Platform (DXP).
In this topic
- Mapping domain host names
- Redirecting to secure URLs
- Restricting login access to the edit environment
- Single Page Application considerations
Mapping domain host names (required)
Environments in DXP are accessed using a set of dxcloud-URLs that are set up and verified according to platform requirements. Examples:
http://appname123inte.dxcloud.episerver.net,
http://appname123prod.dxcloud.episerver.net
Before going live, you need to apply and verify the same DNS settings for the domains that you intend to use with your DXP. This includes creating an awverify record used by Azure, and a CDN-verify record to confirm that you own the domain.
Usually these DNS records are modified:
- CNAME. Creates an alias for a host name.
- A-record. Maps a host name to an IP address.
The following instructions show how to modify the DNS settings. You can use Microsoft DNS Manager if you host your own name servers, or the web interface of your DNS service provider. Or, contact your DNS service provider if you are unsure how to change these settings.
Modifying the DNS settings
Note: The following steps must be done for each domain with which your application should be associated.
Before going live
- Configure your Optimizely CMS to respond to the incoming hostnames you plan to use, such as www.domain.com. Also configure some default URLs like hostname using "*" (preferred), or alternatively:
appname123.dxcloud.episerver.net
appname123-slot.dxcloud.episerver.net
appname123.azurewebsites.net
appname123-slot.azurewebsites.netThe "appname123-slot.dxcloud.episerver.net" address validates the site during deployments.
Mapping of hostnames and URLs occurs at CMS > Admin > Config > Manage Websites.
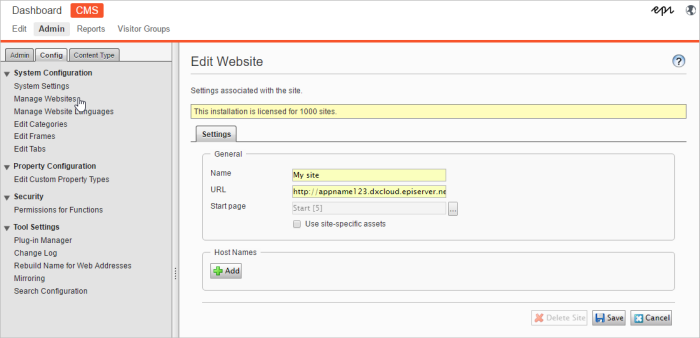
- After you map the hostnames, contact Episerver to inform about which URLs you will use.
- Optimizely sends you an email containing:
- Verification information for CDN and Azure (cloudflare-verify and awverify, these are standard TXT DNS records).
- The A-record pointer to be used later when going live.
- Do the following to verify your ownership of the domain and/or subdomain for the CDN and in Azure:
- CDN. Create a record in your DNS using this format:
cloudflare-verify.DOMAIN.COM IN TXT XXXXXXXXX-XXXXXXXX (the unique numeric value for the TXT record provided by Optimizely).
- Azure. Create a record in your DNS using this format:
awverify.SUBDOMAIN.DOMAIN.com IN TXT appname123.azurewebsites.net.
Example: awverify.www.episerver.net IN TXT dxcwebapp.azurewebsites.net
Note: Verify the settings for Azure and CDN for each domain and/or subdomain to which you want your DXC environment to respond.
- CDN. Create a record in your DNS using this format:
- When done with the DNS updates, contact Episerver again to finalize the verification procedure, and have your verified domains added to the production environment.
When going live
To send traffic from your custom URL to the DXP, you need to create CNAME records in your DNS, pointing to the corresponding DXP endpoint.
- Update the A-record at domain.com so that it points to the IP number you received in the Optimizely email (see step 3 in the previous procedure).
- Add dxcloud.episerver.net to the URL you want to target with CNAME. When this is done, the site is live. Examples:
- www.DOMAIN.com IN CNAME www.DOMAIN.com.dxcloud.episerver.net
- www.customer.com IN CNAME www.customer.com.dxcloud.episerver.net
- beta.client.net IN CNAME beta.client.net.dxcloud.episerver.net
- prod.company.com IN CNAME prod.company.com.dxcloud.episerver.net
- country.charity.org IN CNAME country.charity.org.dxcloud.episerver.net
Redirecting to secure URLs
HTTPS is the secure version of HTTP, adding encryption to the communication between the browser and the editing environment. Redirect in DXP follows industry standard best practices, letting you redirect from a non-secure www URL to a secure www URL through configuration (see below).
The service supports:
- Redirect of non-secure www URL "http://www.domain.com" to a secure www URL "https://www.domain.com"
- Redirect of non-secure root domain "http://domain.com" to www URL "http://www.domain.com"
You can add a redirect rule by modifying web.config in your Optimizely solution.
Example: HTTP to HTTPS redirect rule.
<rule name="Redirect to HTTPS"
stopProcessing="true">
<match url=".*"
negate="false"/>
<conditions>
<add input="{HTTPS}"
pattern="OFF" />
</conditions>
<action type="Redirect"
url="https://{HTTP_HOST}{REQUEST_URI}"
appendQueryString="false"
redirectType="Permanent"/>The service does not support the following by default:
- Using the root domain "domain.com" as the default domain for the site.
- Redirect of TLS/SSL secured root domain "https://domain.com" to another URL.
Note: In many cases, this is not needed because it is seldom that a site visitor would manually enter https://domain.com and start by typing https. Rather they would enter domain.com, which redirects to the secure URL at https://www.domain.com as expected.
Restricting log in access (optional)
To ensure that editing environment is only accessed from approved locations, you can restrict the login to only apply to specified "whitelisted" IP addresses. See Restricting environment access.
Single Page Application considerations
It is important that you correctly set up usage tracking parameters to ensure that the website traffic volume monitoring is correct. For websites using the Single Page Application (SPA) concept, specifically configure the page view tracking, because pages on these websites will not reload during usage. See Consumption metrics for information about configuring page view tracking for single page applications.
Related topics
- Managing DNS records (Microsoft)
- Setting up multiple sites
- Creating Rewrite Rules for the URL Rewrite Module (Microsoft)
 Using routing rules to validate a site before go live/swap (DXP)
Using routing rules to validate a site before go live/swap (DXP)
Last updated: Sep 28, 2021
