Has anyone managed to make a good implementation with Windows Authentication on CMS 12I am trying to upgrade an intranet website to CMS 12 that has personalized content and ImageVault. And I am having a hard time making this work good. I have read the following articles and manage Authenticate users.https://world.optimizely.com/forum/developer-forum/cms-12/thread-container/2022/8/using-on-prem-active-directory-integration-in-version-12/https://learn.microsoft.com/en-us/aspnet/core/security/authentication/windowsauth?view=aspnetcore-8.0&tabs=visual-studioBut I get a lot of claims that do not make any sense to the end users. I managed to translate this and add new claims with the correct name. However, I am unable to remove the old ones with the IDs.
services.AddAuthentication(NegotiateDefaults.AuthenticationScheme) .AddNegotiate(options => options.Events = new NegotiateEvents() { OnAuthenticated = async context => { foreach (ClaimsIdentity identity in context.Principal.Identities) { List<string> claimNameList = context.Principal.Claims.Where(a => a.Type == ClaimTypes.GroupSid).Select(a => a.Value).ToList();
services.AddAuthentication(NegotiateDefaults.AuthenticationScheme)
.AddNegotiate(options =>
options.Events = new NegotiateEvents()
{
OnAuthenticated = async context =>
foreach (ClaimsIdentity identity in context.Principal.Identities)
List<string> claimNameList = context.Principal.Claims.Where(a => a.Type == ClaimTypes.GroupSid).Select(a => a.Value).ToList();
foreach (var name in claimNameList) { var claim = identity.Claims.FirstOrDefault(x => x.Type == ClaimTypes.GroupSid && x.Value == name); if (claim != null) { string translateClaim = null; if (claim.Type == ClaimTypes.GroupSid) { SecurityIdentifier securityIdentifier = new System.Security.Principal.SecurityIdentifier(claim.Value); translateClaim = securityIdentifier.Translate(typeof(System.Security.Principal.NTAccount))?.ToString(); } identity.AddClaim(new Claim(ClaimTypes.GroupSid, translateClaim)); //identity.RemoveClaim(claim); - do not work } } }
foreach (var name in claimNameList)
var claim = identity.Claims.FirstOrDefault(x => x.Type == ClaimTypes.GroupSid && x.Value == name);
if (claim != null)
string translateClaim = null;
if (claim.Type == ClaimTypes.GroupSid)
SecurityIdentifier securityIdentifier = new System.Security.Principal.SecurityIdentifier(claim.Value);
translateClaim = securityIdentifier.Translate(typeof(System.Security.Principal.NTAccount))?.ToString();
}
identity.AddClaim(new Claim(ClaimTypes.GroupSid, translateClaim));
//identity.RemoveClaim(claim); - do not work
var synchronizingUserService = context .HttpContext .RequestServices .GetRequiredService<ISynchronizingUserService>();
var synchronizingUserService = context
.HttpContext
.RequestServices
.GetRequiredService<ISynchronizingUserService>();
await synchronizingUserService.SynchronizeAsync(context.Principal.Identity as ClaimsIdentity); } });
await synchronizingUserService.SynchronizeAsync(context.Principal.Identity as ClaimsIdentity);
});
Also, it looks like Imagevault does not work without ASP.NET Core Identity provider, but I am not sure there.
Did you get this to work?
Has anyone managed to make a good implementation with Windows Authentication on CMS 12
I am trying to upgrade an intranet website to CMS 12 that has personalized content and ImageVault. And I am having a hard time making this work good.
I have read the following articles and manage Authenticate users.
https://world.optimizely.com/forum/developer-forum/cms-12/thread-container/2022/8/using-on-prem-active-directory-integration-in-version-12/
https://learn.microsoft.com/en-us/aspnet/core/security/authentication/windowsauth?view=aspnetcore-8.0&tabs=visual-studio
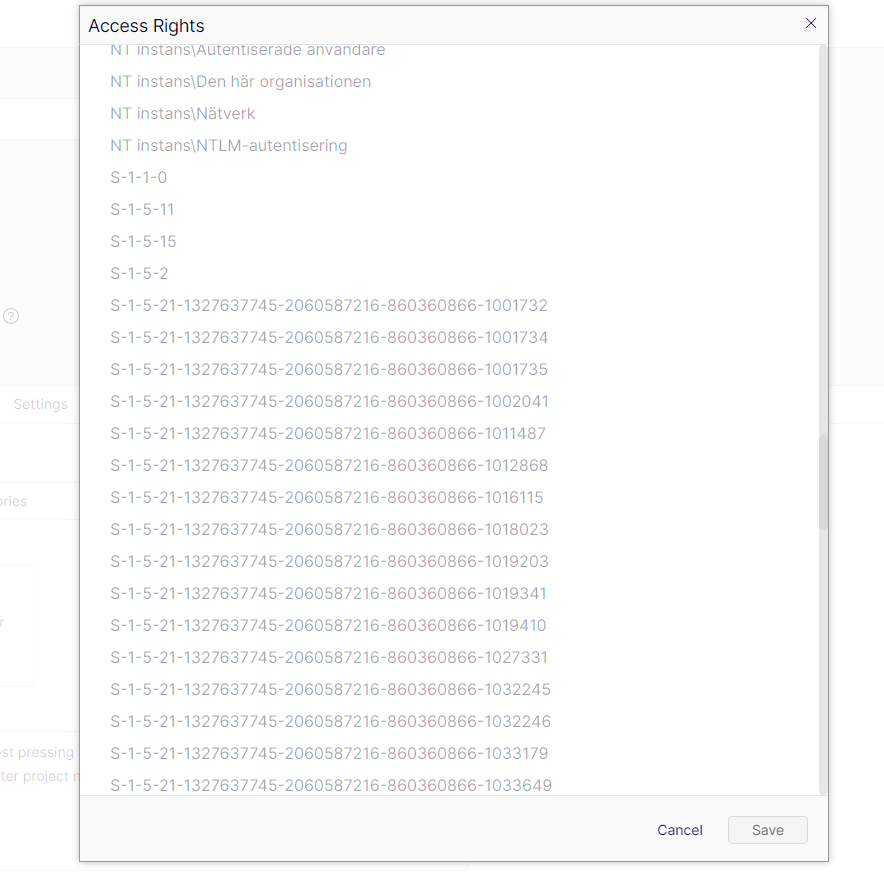
But I get a lot of claims that do not make any sense to the end users.
I managed to translate this and add new claims with the correct name. However, I am unable to remove the old ones with the IDs.
services.AddAuthentication(NegotiateDefaults.AuthenticationScheme).AddNegotiate(options =>options.Events = new NegotiateEvents(){OnAuthenticated = async context =>{foreach (ClaimsIdentity identity in context.Principal.Identities){List<string> claimNameList = context.Principal.Claims.Where(a => a.Type == ClaimTypes.GroupSid).Select(a => a.Value).ToList();foreach (var name in claimNameList){var claim = identity.Claims.FirstOrDefault(x => x.Type == ClaimTypes.GroupSid && x.Value == name);if (claim != null){string translateClaim = null;if (claim.Type == ClaimTypes.GroupSid){SecurityIdentifier securityIdentifier = new System.Security.Principal.SecurityIdentifier(claim.Value);translateClaim = securityIdentifier.Translate(typeof(System.Security.Principal.NTAccount))?.ToString();}identity.AddClaim(new Claim(ClaimTypes.GroupSid, translateClaim));//identity.RemoveClaim(claim); - do not work}}}var synchronizingUserService = context.HttpContext.RequestServices.GetRequiredService<ISynchronizingUserService>();await synchronizingUserService.SynchronizeAsync(context.Principal.Identity as ClaimsIdentity);}});
Also, it looks like Imagevault does not work without ASP.NET Core Identity provider, but I am not sure there.